Checking out the Benefits of LinkDaddy Cloud Services for Modern Companies
Checking out the Benefits of LinkDaddy Cloud Services for Modern Companies
Blog Article
Achieve Company Continuity With Secure Cloud Storage Space Services
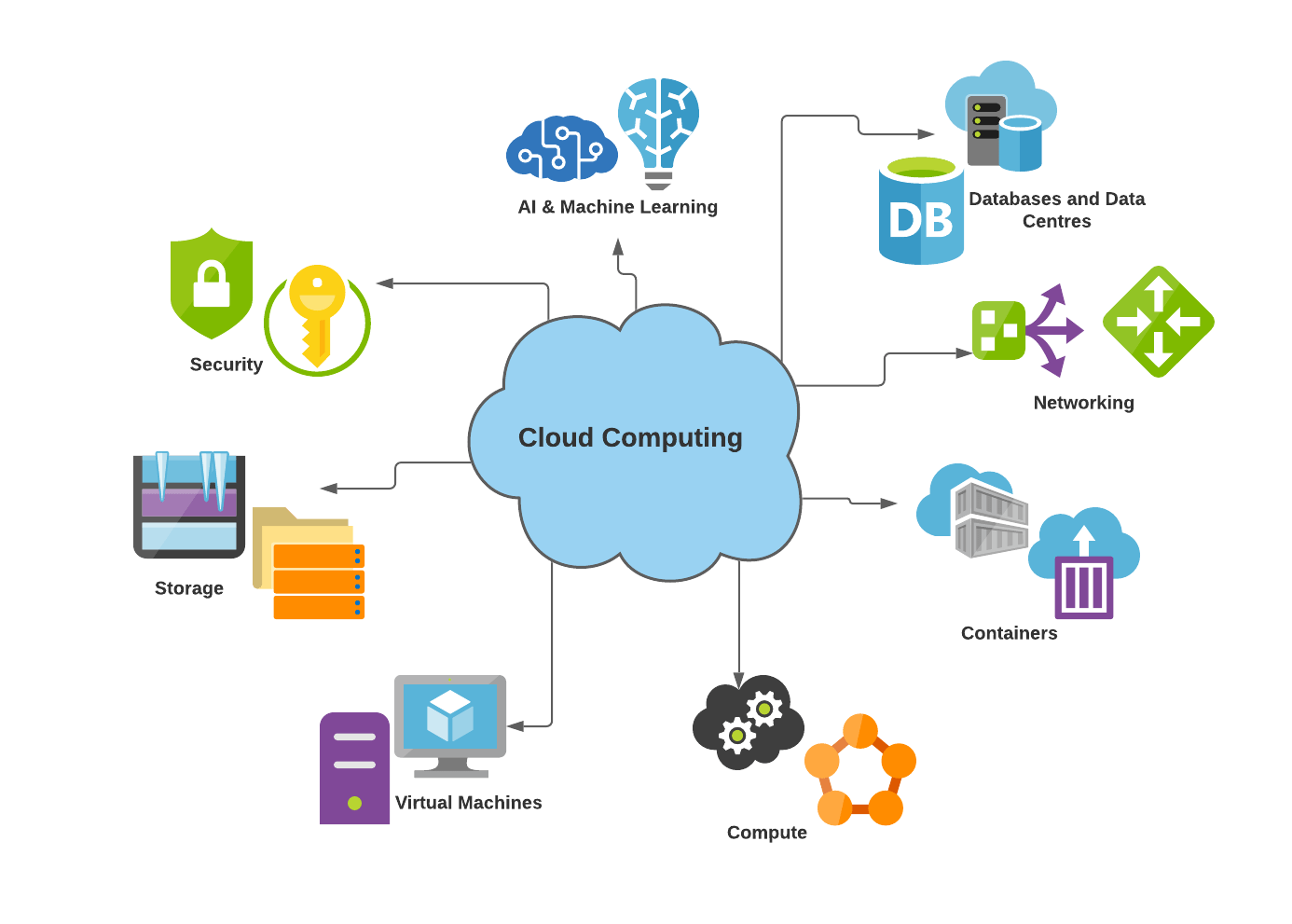
Advantages of Secure Cloud Storage Space
Undoubtedly, protected cloud storage provides companies a plethora of benefits in terms of information security and availability. By keeping data on reputable cloud platforms that use security and sophisticated safety procedures, organizations can guard their details from unauthorized access or cyber threats. In general, the benefits of safe and secure cloud storage space equate into boosted data management, raised functional efficiency, and boosted protection for organizations of all sizes.
Key Attributes for Organization Connection

By distributing data throughout different web servers or data facilities, companies can reduce the risk of information loss and guarantee continuous accessibility to their information. Generally, these vital features work together to develop an extensive business connection approach that safeguards vital information and operations.
Significance of Information Security
In today's interconnected digital landscape, safeguarding sensitive information is critical, making the value of information encryption an essential aspect of maintaining information stability and safety. Information security entails encoding information as if just accredited parties can access and understand it. By converting information into a safe format, file encryption functions as a shield versus unauthorized gain access to, lowering the danger of data violations and cyber risks.
Calamity Healing Techniques
A durable catastrophe healing strategy includes detailing procedures to recuperate data, applications, and IT framework in the occasion of a calamity. One essential facet of an efficient method is routine data backups. By storing data in safe cloud storage services, companies can ensure that crucial details is discover here secured and quickly accessible in case of a calamity.
Picking the Right Company
To make certain seamless service connection and effective disaster healing, picking a appropriate and reliable service supplier for safe and secure cloud storage is extremely important. Guarantee they employ robust encryption techniques, have rigorous gain access to controls, and conform with market laws to guard your information. Additionally, evaluate the supplier's information recuperation capacities.
Your service needs might advance over time, so it's necessary to choose a provider that can suit your growing storage space demands and adapt to transforming situations. By carefully examining these elements, you can pick a cloud storage solution supplier that aligns with your organization's needs and makes certain continuous operations in the face of possible interruptions.
Conclusion
Finally, secure cloud storage space solutions offer vital advantages for achieving service continuity, consisting of boosted Full Report safety functions, seamless scalability, effective partnership tools, robust data backup mechanisms, and disaster healing techniques. Information security plays an essential role in safeguarding sensitive info, while choosing the ideal company is crucial to ensuring conformity with regulations and maintaining functional performance. universal cloud Service. Protected cloud storage space is an important asset in today's electronic landscape for making certain undisturbed service procedures
Information backup devices are essential for protecting versus data loss due to system failures, cyber-attacks, or human mistakes. By dispersing information across different servers or information facilities, companies can minimize the threat of data loss and make sure continuous accessibility to their info.In today's interconnected electronic landscape, protecting sensitive details is paramount, making the importance of data encryption a basic element of preserving data honesty and safety and security. By transforming data into a safe and secure style, security acts as a shield against unauthorized gain access to, lowering the danger of data breaches and cyber hazards.
Conformity requirements and data protection laws usually mandate the usage of encryption to safeguard delicate info, highlighting its vital role in modern-day data security approaches.
Report this page